To stay cyber secure, organisations need to have robust Security Information and Event Management (SIEM) systems in place. My internship helped KPMG to achieve just that by strengthening their SIEM capabilities.
As part of my Master of Computing degree, I undertook a three month internship at KPMG. Throughout this internship, I worked on a range of projects for both internal tools and on behalf of clients.
In one of my favourite projects, I was tasked with working with KPMG’s internal cyber security team to integrate their tools with new threat intelligence data sources. To demonstrate my work, I was asked by the ANU to produce a poster, and a pitch video.
SIEM and CTI
SIEM tools provide real time threat monitoring by analysing network traffic and log feeds to find indicators of compromise (IOC). IOC are signs that a system may have been breached. Looking for IOC in logs enables organisations to respond quickly to real-time alerts of suspected breaches.
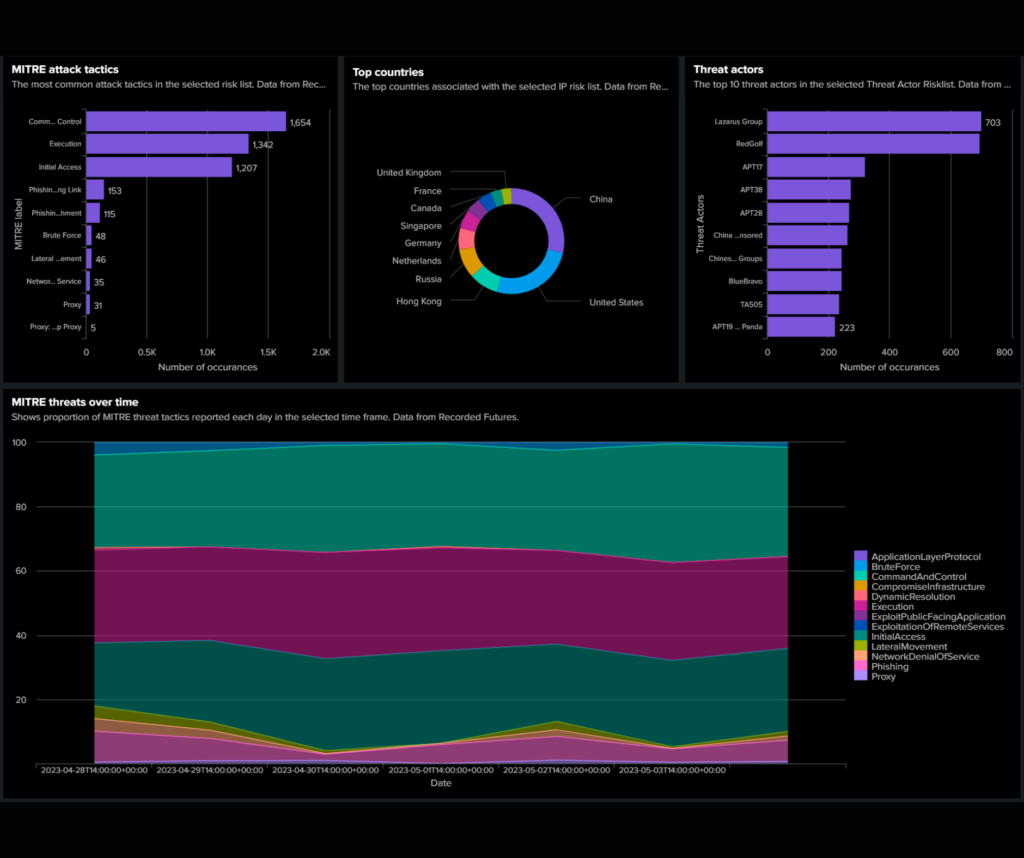
SIEM tools are powered by cyber threat intelligence (CTI), which provide the IOC to search for. KPMG recently invested in a new source of CTI that they wanted to integrate into their SIEM tool.
Using new CTI sources
I was tasked by KPMG’s Cyber Security Operations team with integrating this new CTI source into their SIEM tool, with the aim of boosting the system’s threat detection capabilities and empowering the team with insights into emerging threats.
To integrate with the new data source, I configured a third-party connector in KPMG’s SIEM environment. Next, I assessed the threat data to determine the kinds of insights I could extract from it. Based on this analysis, I developed a threat intelligence dashboard which enabled KPMG to easily understand the threat landscape.
Next, I configured and tested IOC detection rules for accuracy, efficiency, and validity. These rules generate alerts when IOC are found and indicate that a system may be have been compromised. The rules that passed the tests are now ready to be activated, which will further enhance KPMG’s cyber security posture.
Results and benefits
Integrating this CTI source into KPMG’s SIEM tool benefited multiple stakeholders. The security team gained enhanced cyber security capabilities, and their management gained additional oversight. KPMG employees now have added protection, and KPMG’s clients have peace of mind about their data and systems.
I have strengthened KPMG’s SIEM system by integrating new CTI sources, configuring new detection rules, and developing insightful dashboards. These efforts have bolstered the organisation’s ability to resist ever-evolving cyber threats.
The views expressed in this blog, poster and video are that of the author alone.